Search results for: “SECURITY”
-

Reliable Crypto Signals Services you Should Use in 2022
When you’re trading cryptocurrency, getting a reliable crypto signals provider is no longer a matter of choice. It’s a necessity. Crypto signals are notifications that inform you when a particular crypto asset is about to experience a significant price change. Many crypto signal providers offer a variety of services, including market analysis, news, and trading…
-

Smart Home Devices You Should Get in 2022
Fast-paced technological innovation is the defining quality of the last decade or so. It affects everything, from the big business world to transportation to people’s homes. Smart home devices are among the coolest and most helpful novelties of recent years. Their influence is clear even from Amazon Alexa’s place in popular culture—she is basically a…
-

Tech Maintenance Procedures Every Student Should Know
Laptops and smartphones have become irreplaceable in student life. Whatever their price, they provide access to a well of infinite knowledge. Students can use them to get help with college physics, learn new languages, or sign up for educational courses. All sorts of valuable academic help platforms are available through the medium of technology. That’s…
-

What Are the Benefits of Identity and Access Management (IAM)
Identity and access management should be a key strategic and technical priority for businesses in 2022. Identity and access management or IAM is a broad term. IAM describes internal organizational processes focused on managing user accounts and network resources, including access rights for users, systems, and applications. The broad goal of IAM is to manage…
-

Introduction to Scratch Disk Management
If you are a regular user of energy-demanding, complex apps such as Photoshop or Adobe, you’ve probably heard about the scratch disk. Pop-up messages saying that the scratch disk is full are annoying and frustrating, especially if you don’t know what the problem is. This article defines scratch disk, explains why it is needed and…
-

Safeguard Your Systems: How to Prevent Hacking
Your desktop computer, laptop, and tablet — even your smartphone — are juicy targets to seasoned and newbie hackers alike. But what makes one individual or company a more attractive target than another? Are there any common threads that dictate how hackers pick their victims? Suspect someone is trailing your digital path? To help tailor…
-

4 Valuable Tips When Looking for Relevant FS22 Mods
The long-awaited Farming Simulator 22 game is coming soon. GIANTS Software might have taken a while to prepare the new title for its fans, but November 22 is pretty much a few days away, and that is when the game becomes available on multiple platforms, including macOS, Windows MS computers, PlayStation, Xbox, and even PS…
-

Creating An Assured Web Presence
A digital presence is practically non-negotiable for businesses of all sizes in the modern economy, yet that creates significant risk for non-tech-savvy enterprises. Data, and its management, can be a huge risk for businesses; one Forbes study found that a data breach reduced stock price by 7.72% on average. While this seems like a big company problem,…
-

5 Clever Ways Companies Counter Hackers
You’ll notice that there are more cybercrime reports nowadays. Many hackers are using ransomware to extort money from small, medium, and large organizations. In addition, hackers are stealing company secrets and client data through spyware and Trojans. Some hackers take over systems with rootkits and open backdoors for keyloggers and other malware. To protect themselves…
-
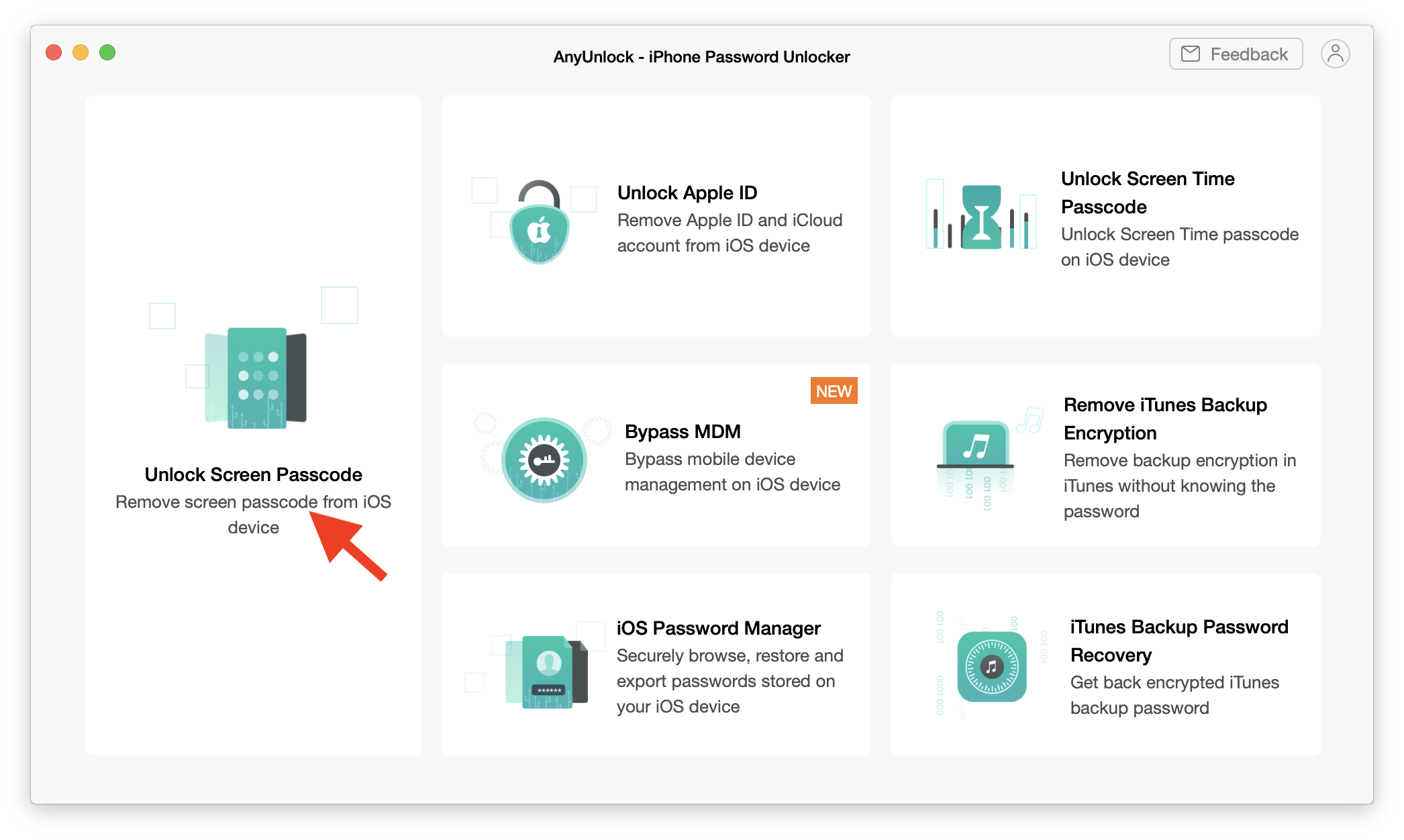
Lost Your Passcode? Here’s How to Unlock Your iPhone
Getting locked out of your phone without a way to get in is an experience no one should have to go through. However, it sometimes happens to the best of us. In case you are already in this situation, you should know there are ways to get back in and take control of your device.…
-
The Advantages AI Offers Online Casinos
AI can easily summon images of sci-fi films and books, but today artificial intelligence is being increasingly used in a wide variety of fields. Fighting crime, including fraud, money laundering and other transgressions in casinos, is no exception. Chip Dumping and Money Laundering Everybody likes winning big at poker or blackjack, but sometimes wins are…
-

Let Us Be Your Guide for Buying a New Laptop
As most users become increasingly demanding of their laptops, it is vital to make the right choice when it comes to purchasing a new laptop. An over-the-top laptop can cost you significant extra budget for features you will not use. Similarly, if you end up with a laptop that is not fit for purpose and…
