Search results for: “data security”
-

7 Ideas to Guide Children in Using New Technologies
Children have access to the Internet from their early stages. In many houses, smartphones, tablets or computers naturally coexist with other toys. In fact, it is very common for toy companies develop specific computers for children with child interactive games. Because children live with these devices and know how to handle them without receiving any…
-
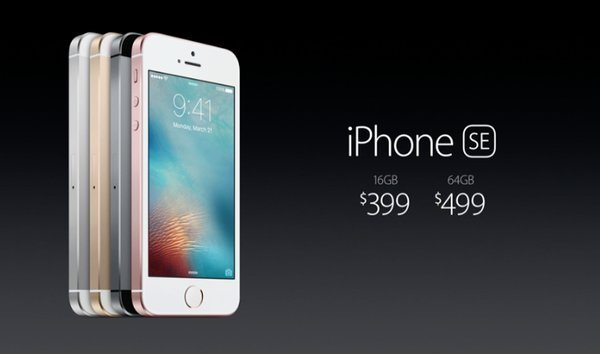
iPhone SE, 9.7″ iPad Pro, iOS 9.3 & Highlights From The Apple Event
Apple, today, announced majorly two new products and the latest iOS 9.3. Ironically, Apple decided to downsize its products at a time when everyone thought Apple devices were getting rather bigger. Just as the iPhone 6S gets smaller in the form of iPhone SE, the iPad Pro too receives a size cut and the 9.7″…
-

A Comparitive Study To Evaluate GetResponse And Benchmark
In online marketing, entrepreneurs must prioritize site optimization program to accelerate web traffic with the sole purpose of winning more reliable customers. To be frank, it is not an easy task to convince a customer to buy your products. You must be dedicated with specific plans on how to chalk out more constructive product promotion plans…
-

Tecno Phantom 5 Review: Simply Put, a Masterpiece
Tecno Phantom 5 isn’t Tecno Mobile’s first attempt at dabbling into premium smartphones but this new addition to the Phantom product line breaks away from the norm. Critics and fans alike have expressed diverse opinions about this device but one thing is certain, we at Geek NG love it. Tecno Phantom 5 will change the…
-

How to Totally Disable Windows 10 Automatic Updates
For some of us who do not have unlimited internet access, it’s very crucial to manage, not only how applications connect to the internet, but also how our OS handle system updates. Default Windows 10 settings doesn’t really leave you much choice, updates will be downloaded anyway whether you like it or not. Microsoft probably…
-
You Should Change This Windows 10 Update Settings Now
That person at Microsoft who assumed it was a pretty good thought to to allow users to update their OS through P2P conceived a terrible, evil idea. In case you don’t really know what this means, it simply means the default Windows 10 settings will allow someone, somewhere else on this planet access your downloaded…
-
Cuts in Smartphone Pricing as Lenovo Unveils New Yoga Laptop Series
Global leader in mobile communications Lenovo has reduced the prices of its P70 and A5000 smartphones in Nigeria, in a drive to deliver rich mobile experiences and superior smartphone technology to more Nigerians. Through this offer, customers can now purchase the Lenovo P70 or A5000 smartphones from accredited retail outlets nationwide at a recommended retail…
-

Lenovo Tab A7-30 (A3300-HV) Hands on Review
For about two weeks, I’ve played around with the Lenovo Tab A7-30, a 7″ tablet relased mid last year. Generally, a lot of people prefer smaller tabs like this that can as well function as smartphones and this particular product fits that description. However, it should be noted that Lenovo Tab A7 has a WiFi…
-

WordPress Hack: How I Regained Access and Recovered the Site
I was working on this website that night when I was logged out. I tried logging back in and WordPress told me my IP address had been locked out due to several login attempts. I was confused at first and then realized Jetpack has the feature enabled. Several log in attempts? When? By who? My…
-

How to Protect Yourself from Identity Theft
I’d like to thank Geek.ng for publishing my article on their website. I’ve found their site to be an amazing resource to aid anyone in their ventures with technology. If it’s a how-to you’re looking for, news, blogging tips, or even an answer to some of your tech-related questions, their page is the place to…
-

Some Facts About Visa Learned from Tech Bloggers Roundtable Meeting
Unless one knows exactly what VisaNet is all about or you’ve had someone explain to you how things work, an average person probably has no idea how huge the technology behind card transactions could be. While most of us are conscious about our ATM card security, things are happening behind the scenes and Visa hosted…
-

How to Root Tecno Boom J7 in One Click
Rooting Tecno Boom J7 is pretty easy and you don’t even need a PC to get it done. All that’s needed is the required APK file and you should be done in less than 3 minutes. Also read: Tecno Boom J7 Review: The Android Music Phone You Would Like By reading this article and following…
