Search results for: “computers”
-
7 Best Websites to Scan Your Files Online For Viruses
Everyday on the Internet, we are getting latest information on advanced technology, gadgets, new software programs for different purposes and much more but with all these, we are also getting some news about viruses, malwares, trojans and lots of other malicious programs that spoil our computers, leading to instability of system. There are many ways that viruses,…
-

mSpy Review: Best iPhone Stealthy Monitoring Application
In this age where employees leak corporate secrets, where it’s reported that 75% of employees steal from workplace and 60% inventory losses are brought about by employees, it’s only right to protect your business and prevent bankruptcy by monitoring your employees business lines. Unless you have every single reason to trust your employees totally, tracking…
-

5 Best Antivirus Software For Windows 8 In Year 2013
Windows 8 is quite one of the best windows operating system till date and it has been the most impressive operating system for most computer users. A computer without an antivirus software is quite incomplete because it can easily get infected with virus at any point in time and you are likely to lose those…
-

5 Free Android Apps that Make Reading on Mobiles Fun
Amazon’s Kindle may be the ultimate e-Reader for voracious readers, but most people read digital novels, stores, and articles on their mobiles. Smartphone users can access and read any book they want, anytime. While one may not want to read Proust’s Remembrance of Things Past on an Android device, reading short stories and light novels…
-

List of Must Have Software Programs For Computer Repair ToolKit
One day you may regret not having the right software toolkit when you run into a situation whereby you find yourself stuck, completely out of options but to repair your personal computer with common software programs you’re supposed to have in the first place. Since the day I tried to remove screws with a nail…
-
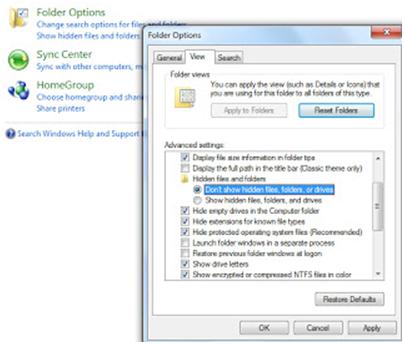
5 Simple Steps to Secure your Personal Computer
Computer insecurity has been widely common since the importance of computers became globally known. Many security upgrades were taken to ensure maximum security on personal computers, yet security breach is still at large and it seems like it can never be eradicated. Computer insecurity has brought about countless chaos and frustrations to many victims including…
-
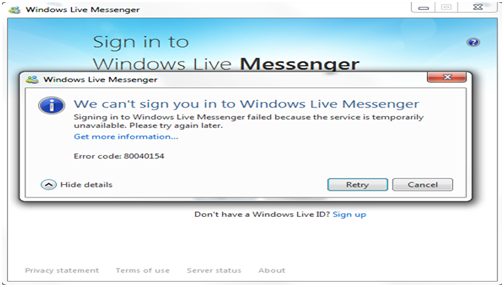
How to Fix Windows Live Messenger (MSN) Error 80040154
Lately, MSN Messenger has been named as Windows Live Messenger. This program is the instant messaging service that every user can make use of, whose system is running on Windows operating system. Windows live Messenger has been deployed in many consoles such as Xbox 360. Zune HD, Blackberry operating system and Symbian OS 9.x are…
-

Fix: Get ‘Copy’ & ‘Paste’ Functions Re-enabled in Windows
Copy and paste are two fundamental commands of Windows which enable you to take a file from one location to another. The contextual menu available in every Windows program will enable the user to ‘copy’ a file from any location and ‘paste’ the same file in another location of the user’s choice. ‘Ctrl+C’ & ‘Ctrl+V’…
-

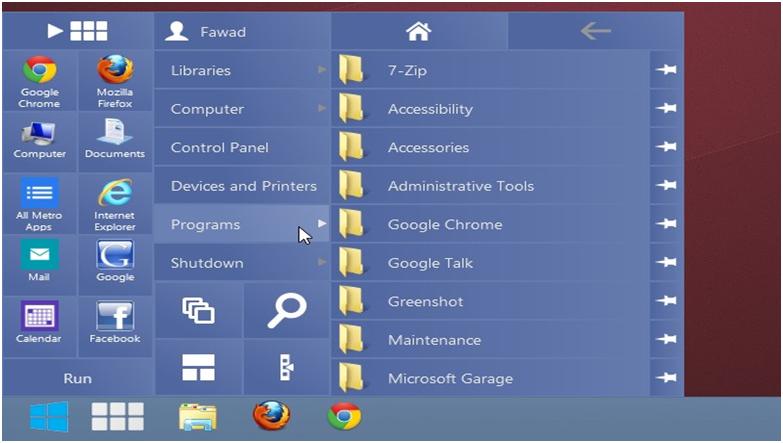
Windows 8 Starter Guide: Get to Know W8 Sooner and Better
Launch and release of Windows 8 would excited a lot of users, but when it came to the usage of this same OS on their systems, it was disappointing. The reason is the completely new interface, with the elimination of traditional interface elements. It is not being long that Windows 8 was released and perhaps,…
-

Simple Techniques to Use Windows 7 More Efficiently
Windows 8 seemed to be a hot cake for a long time now. However, after the release and hands on experience of W8, most of the users are not willing to switch their operating system from Windows 7 to Windows 8. Existing users have decided to stick to Windows 7 and new users are planning…
-

What Type of Business Security Solution is Best for You?
In a world where data security is increasingly important, you need to keep your business safe. Hackers, both domestic and international, are constantly looking to take advantage of or exploit flaws in your company’s security. This can enable them to access sensitive data and customer records or even damage your business itself through a full-scale…