Search results for: “data security”
-

Cyber Security Measures You Should Take When Working Remotely
Digital security is something that needs to be carefully considered by anyone who is involved in remote working, whether that is the employer, client or the employees themselves. This includes those who occasionally work from home instead of commuting to the office, as accessing the business network remotely might lead to issues with security. The…
-
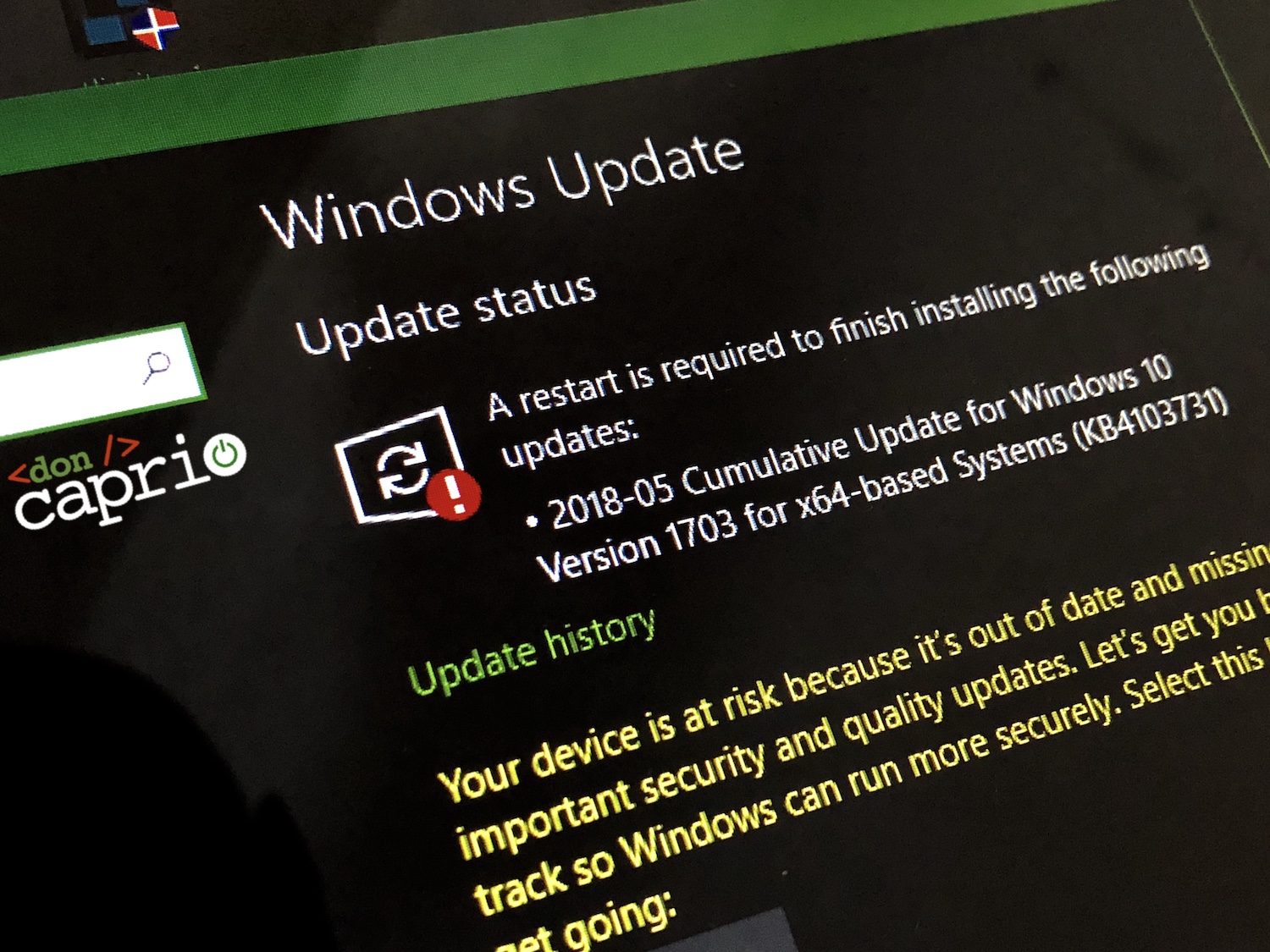
How to Stop Excessive Data Usage on Windows 10
One of the reasons a lot of people downgraded from Windows 10 back to Windows 7 is the excessive data usage that seems hard to control. Unlike previous versions of Windows, Windows 10 seem to consume more data. People with unlimited Internet subscription might not notice, but when you have to manage a 10GB data bundle…
-
5 Effective Ways to Improve IoT Security in 2018
The IoT and IIoT sectors are growing at a rapid rate as connected devices are constantly released for home and office use. It has been predicted that the number of active wireless connected devices will exceed 40 billion by the year 2020. Despite this development, security remains a serious issue that must be addressed promptly.…
-

Security Master Review: A Complete Security Suite For Android
There’s a reason Google keeps issuing security patches to Android OS like every month. There are flaws that keep getting patched but unfortunately, these patches don’t make it to every Android device. To be safe, it’s best to put the security of your device into your own hands even if you get these patches every month.…
-

Internet Security: How to Stay Safe On The Internet
Either directly or indirectly, almost everything we do these days requires the internet or somehow connected to the world wide web and the internet seems to be growing too fast for most people to comprehend. There are risks involved with using the internet like virus attacks, malware, spyware and data theft which has affected a…
-

Android Security Tips: Keeping Your Android Device Safe
There is no debating that the Android operating system is the one of best in the world of smartphones and as with any software, it is susceptible to harm. You need to ensure a lot of protection on your android device and with the following steps you can ensure that nothing unforeseen happens to your…
-

Steganos Online Shield 365 Review: Online Security & Privacy Software
Most regular internet users do not really care about securing the internet activities. While some believe online security is only for advanced internet users, others are not even aware of the dangers of surfing the internet unprotected. Securing your internet activities and encrypting transmitted data doesn’t only protect you from malicious websites that steal information…
-

What Type of Business Security Solution is Best for You?
In a world where data security is increasingly important, you need to keep your business safe. Hackers, both domestic and international, are constantly looking to take advantage of or exploit flaws in your company’s security. This can enable them to access sensitive data and customer records or even damage your business itself through a full-scale…
-

Common Security Risks With Cloud Computing
Ever since the emergence of cloud computing, it has changed the way we use the internet and our personal computers. Lots of enterprise totally rely on cloud computing to better facilitate their business and quite a lot of regular internet users depend on it for basic things such as music and more. With so much…
-

Encryption: The Key to Data Protection
Encryption key management is today’s safest way to protect computer data and computer hardware like desktop, laptop and other data storage devices from constant attacks by hackers. The volume of hacking into integrated systems continues to increase even with the use of many of the software programs intended to create a firewall to protect sensitive…
-

Introduction to Top Five Cloud Computing Security Issues
One of the most and frequently talked about aspects of the IT industry is in relation to cloud computing. It has grown from just mere terms to take its place as the leading segment within this industry. Cloud computing allows users to execute and operate software applications which is stored on the internet. Lots of…

